Enable IPv6 On Toastman-Tomato Routers
Just realized today that I’ve been running without IPv6 enabled on my Linksys E900 v1.0 that is running TomatoUSB firmware from Toastman (v1.28.0503.7 MIPSR2Toastman-RT-N K26 USB VPN).
A little searching found Comcast’s IPv6 page, a Comcast IPv6 test page, and a very excellently written forum post by koitsu.
A little more searching led me to the below images with instructions. Worked great.
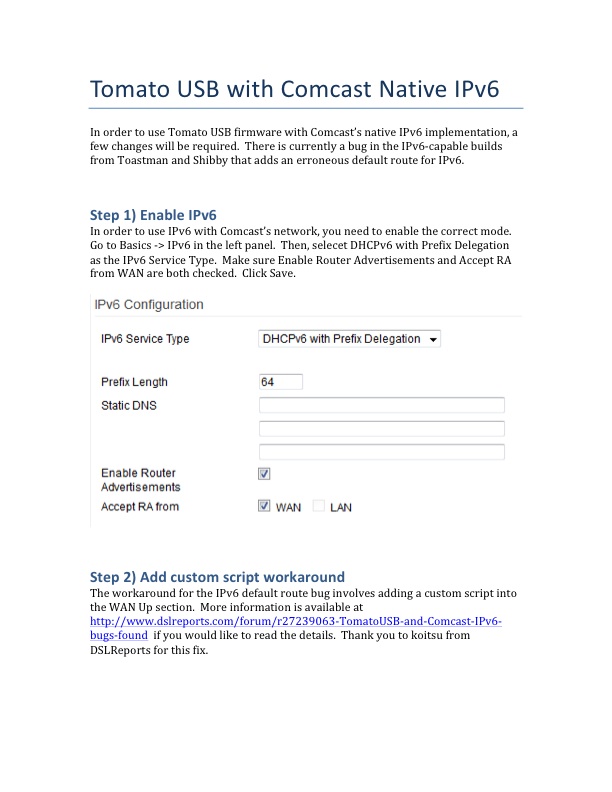

And my results:
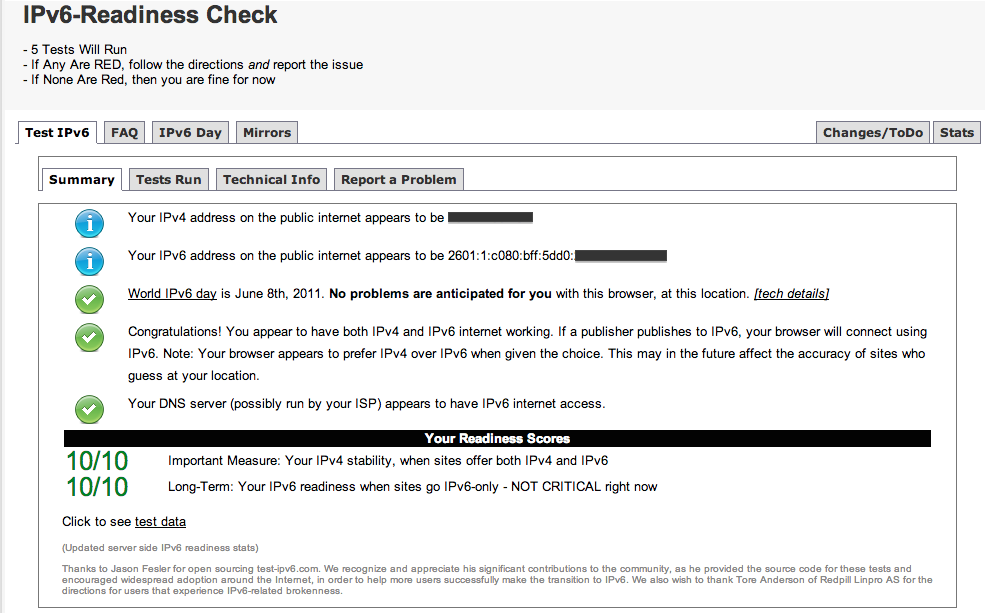
And keep reading!
After setting this up, I noticed a lot of error messages in the log
Mar 2 11:45:22 RT-c8d719a52a51 user.warn kernel: printk: 782 messages suppressed.
Mar 2 11:45:22 RT-c8d719a52a51 user.warn kernel: Neighbour table overflow.
Mar 2 11:45:25 RT-c8d719a52a51 user.warn kernel: printk: 329 messages suppressed.
Mar 2 11:45:25 RT-c8d719a52a51 user.warn kernel: Neighbour table overflow.
Mar 2 11:45:29 RT-c8d719a52a51 user.warn kernel: printk: 518 messages suppressed.
Mar 2 11:45:29 RT-c8d719a52a51 user.warn kernel: Neighbour table overflow.
Mar 2 11:45:34 RT-c8d719a52a51 user.warn kernel: printk: 338 messages suppressed.
Mar 2 11:45:34 RT-c8d719a52a51 user.warn kernel: Neighbour table overflow.
Mar 2 11:45:40 RT-c8d719a52a51 user.warn kernel: printk: 374 messages suppressed.
Mar 2 11:45:40 RT-c8d719a52a51 user.warn kernel: Neighbour table overflow.
Some more research led to another article by koitsu. Adding the following values to my Administration -> Scripts -> Init script fixed the problem
echo 512 > /proc/sys/net/ipv4/neigh/default/gc_thresh1
echo 1024 > /proc/sys/net/ipv4/neigh/default/gc_thresh2
echo 2048 > /proc/sys/net/ipv4/neigh/default/gc_thresh3
echo 512 > /proc/sys/net/ipv6/neigh/default/gc_thresh1
echo 1024 > /proc/sys/net/ipv6/neigh/default/gc_thresh2
echo 2048 > /proc/sys/net/ipv6/neigh/default/gc_thresh3
This also works in lieu of the above modifications. Place this line in Administration -> Scripts -> Firewall and reboot. Been running it and it is working well.
ip6tables -A PREROUTING -t mangle -p icmpv6 --icmpv6-type neighbor-solicitation -i `nvram get wan_iface` -d ff02::1:ff00:0/104 -j DROP